Reducing the SecOps workload with an AI-powered Cybersecurity Solution.
1. CREATE AGENT POLICIES
An agent policy was created in Elastic Fleet for each operating system (Windows – MacOS) that needed monitoring.
2. ADD INTEGRATIONS TO POLICIES
Various integrations were added to these policies to log specific components such as Windows event logs, network packets, etc.
Both policies for both Windows and MacOS had the “System,” “Network Packet Capture,” and “Endpoint Security” integrations added. An additional integration named “Windows” was added to the Windows policy to capture Windows event logs.
3. CONFIGURE INTEGRATIONS
All integrations were then configured to capture the necessary data. The endpoint protection integration was also configured as an antivirus, taking action to detect and block threats.
After setting up the agent policies, Elastic Agents were deployed on Formica employees’ laptops. Once installed, the Elastic Agents sent data to Elastic Cloud, securing the laptops.
At the time of writing this article, Elastic had 1051 pre-made detection rules to support your SIEM. To determine which rules were relevant, the MITRE ATT&CK framework was used. Specific threat groups targeting the technology sector were identified, and rules for the attack techniques these groups use were activated. This way, alerts are generated when these attack methods occur on the laptops.
Elastic Security includes numerous out-of-the-box dashboards that provide insights into your environment. These dashboards display alerts, the number of incoming logs, and an overview of the protected laptops.
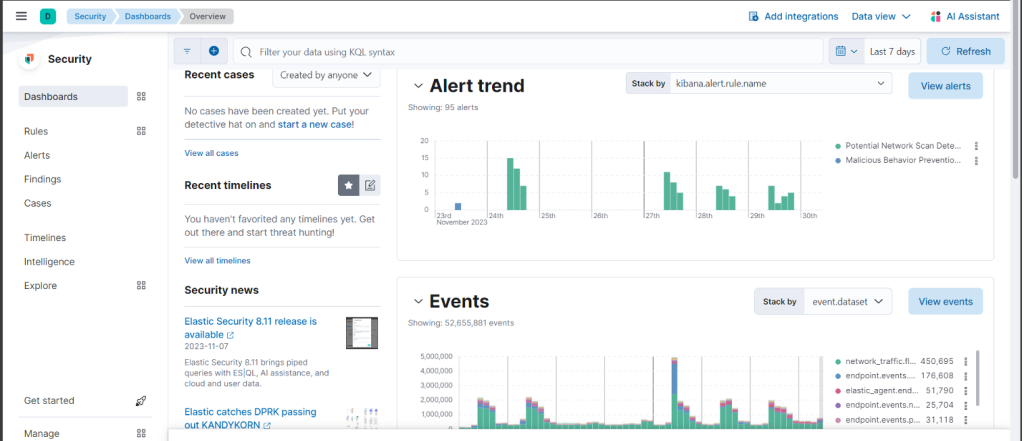

Elastic Security in action
Recently, there was a critical alert about an endpoint showing a suspicious launch agent named ‘ksinstall.’
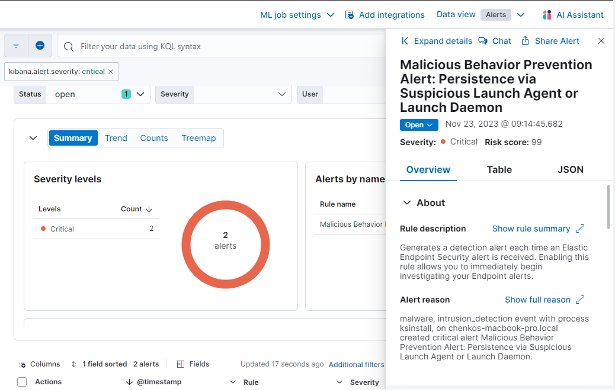

1. First actions
Upon noticing this alert, details were examined in a timeline. Filtering on the “ksinstall” process revealed extensive information about all actions taken by ksinstall on the host.
Initially, it was unclear whether this was malicious or not.
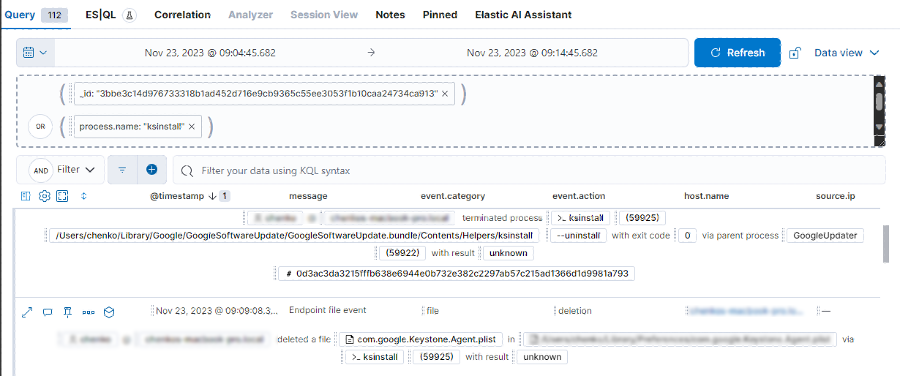

2. Using the AI assistant
To further and quickly investigate the situation, the decision was made to use the security AI assistant introduced by Elastic in June 2023. The AI assistant operates using the well-known GPT-4 from OpenAI. To use the AI assistant, the following setup is required:
1. OpenAI developer account
Start by obtaining an OpenAI developer account to generate an API key for setting up the connector in Elastic Cloud.
2. Credit card top-up
Perform a one-time top-up via a credit card to add credits or tokens to your account, granting access to the GPT-4 model. You can only generate your API key after this top-up.
3. Elastic Cloud Configuration
Once you have the API key, open the AI assistant in Elastic Cloud, and it will guide you in setting up the connector.
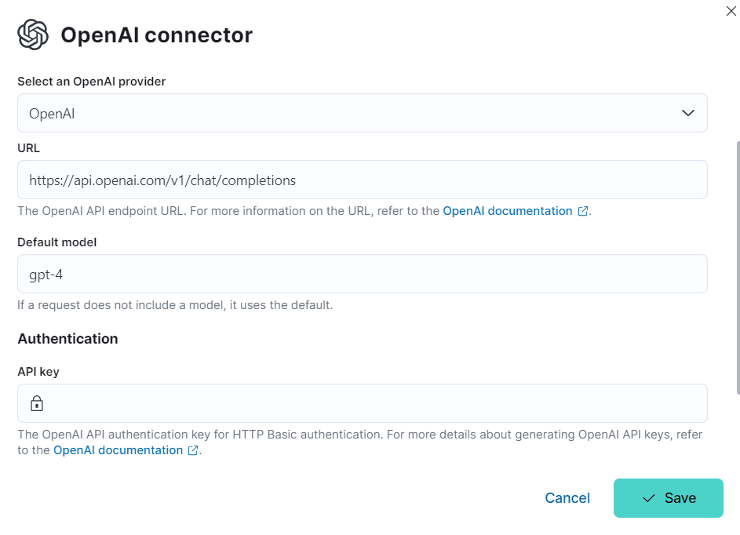

4. Elastic AI assistance
Vraag 1 – Alert Summary
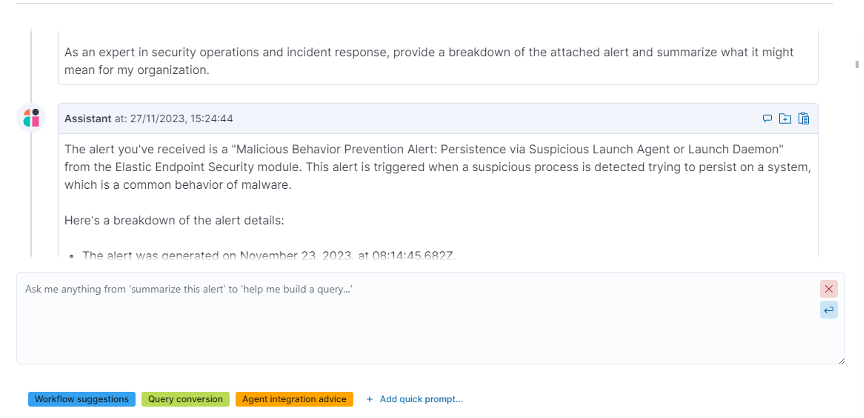

For the first question, we used one of the pre-made Elastic prompts to provide a summary of the alert and what it could mean. This gives a quick and clear overview of what is happening.
Vraag 2 – Workflow Alert Investigation
Next, we asked for a workflow to investigate the alert.
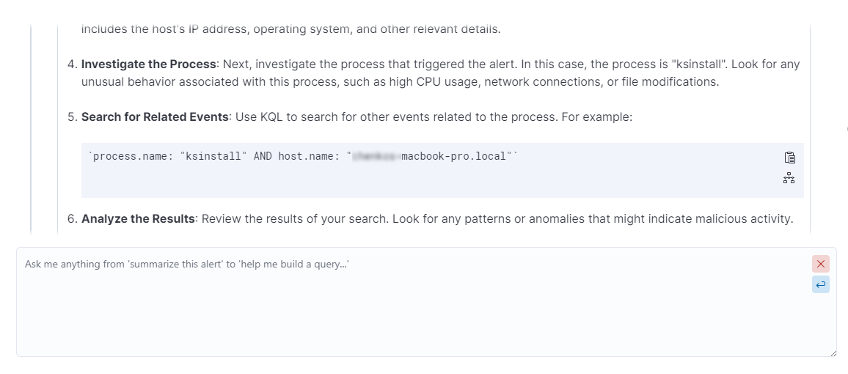

This workflow includes KQL queries that can be directly copied into Elastic “discover” or added to the timeline.
We placed these in “discover” and then displayed the fields ‘process.name’ and ‘process.args’ to quickly see what this process did to the system.
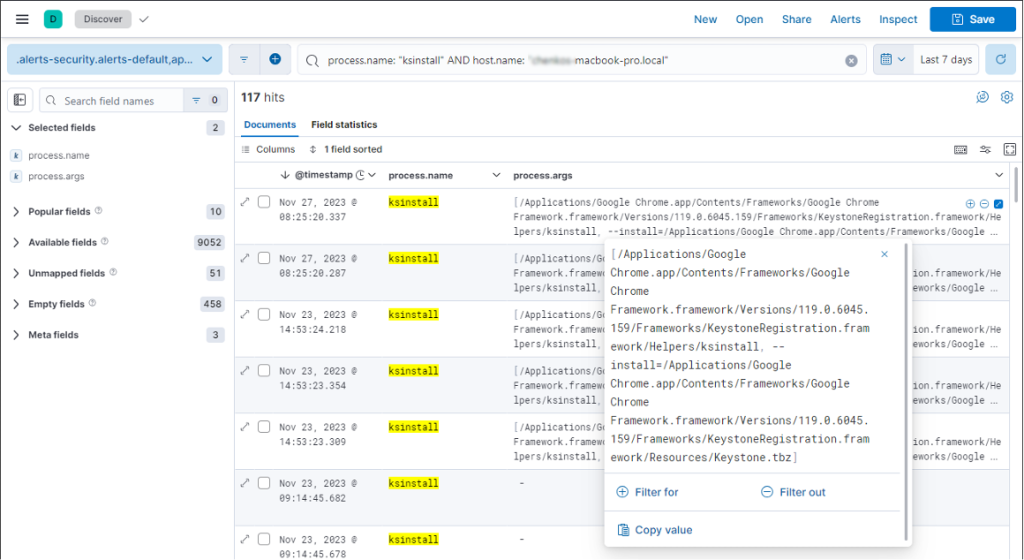

From this, you can see that ksinstall attempted to install the file Keystone.tbz. This file is in a Google Chrome folder, and ksinstall was a child process of Google Chrome.
Vraag 3 – Process arguments clarification
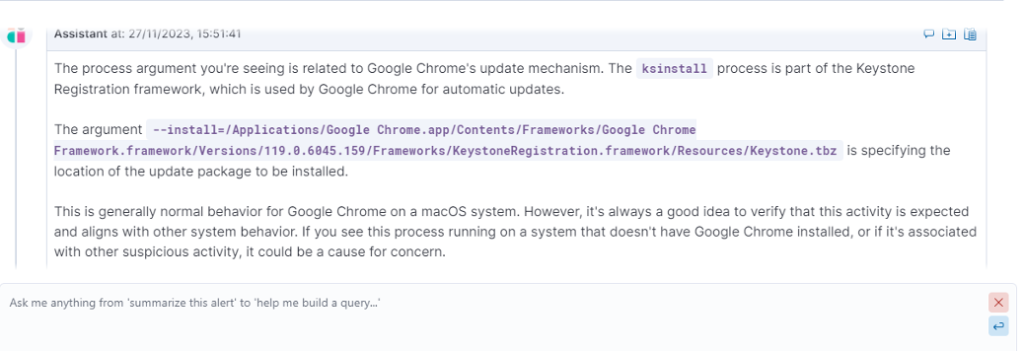
To clarify this, we asked the AI assistant what Keystone.tbz is and whether it is normal for Google Chrome to do this.
You quickly get an answer that this is part of the Chrome update process.

Vraag 4 – Malicious examples
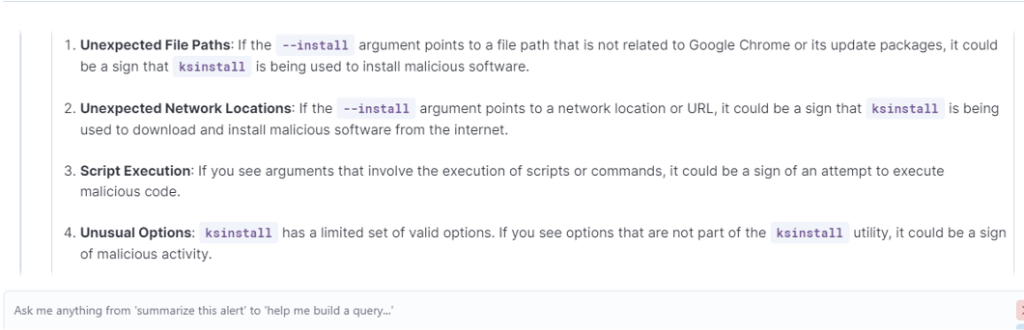
Furthermore, we asked for examples of things that are suspicious and require investigation.
While continuing to search in the discover, none of these four points came up. So, we asked the assistant a final question to conclude.

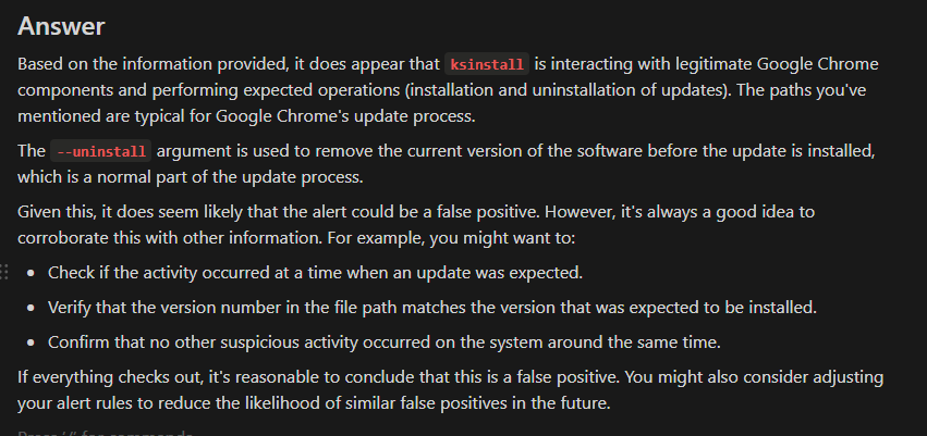
Vraag 5 – Wrapping up
This was the answer that came out, and thus, we can conclude that this alert is a false positive.

3. RESULTS
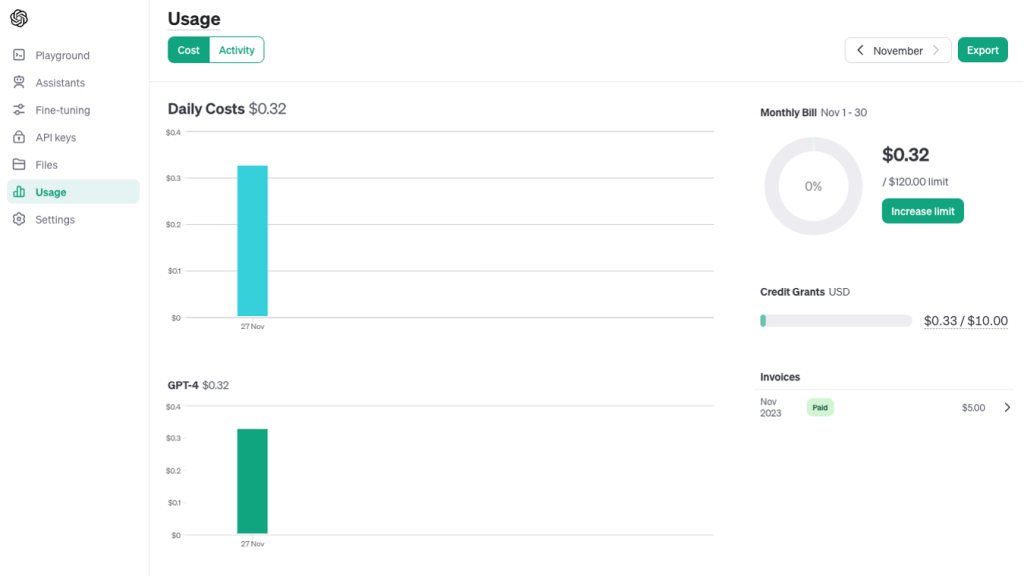
With the help of the AI assistant, the alert was quickly addressed. The total cost of the conversation with the AI assistant was $0.32.

CONCLUSION
The use of Elastic Security with the AI Assistant significantly increases the productivity and efficiency of security engineers and analysts for a minimal investment.
Elk Factory – elite Elastic Partner
Elk Factory is the Elastic partner to implement the Elastic platform. We aim for a win-win! We look at how this platform can make your company benefit the best, in return we can enjoy another satisfied customer!
Get to know us and contact us without obligation.
