
ZERO-DAY EXPLOIT FOLLINA – MICROSOFT OFFICE
On Monday, May 30, 2022, Microsoft issued CVE-2022-30190 regarding the Microsoft Support Diagnostic Tool (MSDT) in Windows vulnerability, which is an exploit using the MS Word remote template tool to fetch an HTML file from a remote web server and executed as code in PowerShell. This feature lets attackers use infected MS Word documents to run remote code using the MS-MSDT protocol URI scheme on a victim’s computer.
In this test, we will use the Elastic Security endpoint protection to stop the attack from executing as well as use its diagnostic tools to find the cause of the infection. To do this we will use John Hammond’s GitHub project to simulate the infection on our windows 11 victim running Elastic endpoint protection. This GitHub project will allow us to create the infected word document via an attacking Kali Linux machine which our unknowing subject will execute.
In most cases such documents would be distributed by bulk email, to quickly spread them to as many people as possible without any effort.
INFECTING THE COMPUTER
The first step is to download the infected Follina Document to our target machine.
When we open the document, nothing happens yet, as we will have to enable editing first. However, there are ways in which the exploit can launch remote code execution even when not enabling editing, but simply by opening the document.
In this case, the connection to the remote server will only happen once the document has been enabled for editing. Fetching the link to the remote server on our kali machine and sending our payload to the victim.
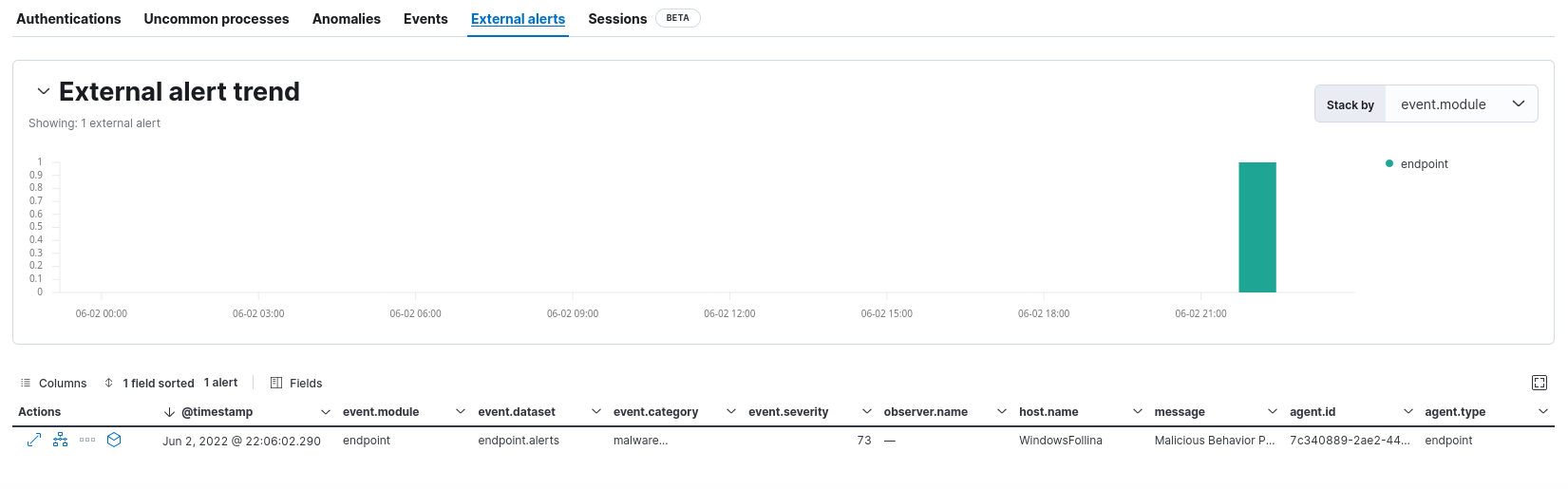
The Elastic Endpoint instance triggered an alert about an attempt to execute a malicious file on the windows 11 machine.

ELASTIC SECURITY AT WORK
We kick off our investigation in Kibana and see that the msdt.exe has been launched by a windows process, which is what we used to launch the payload. However, this process has been terminated by Elastics endpoint protection preventing remote code execution.
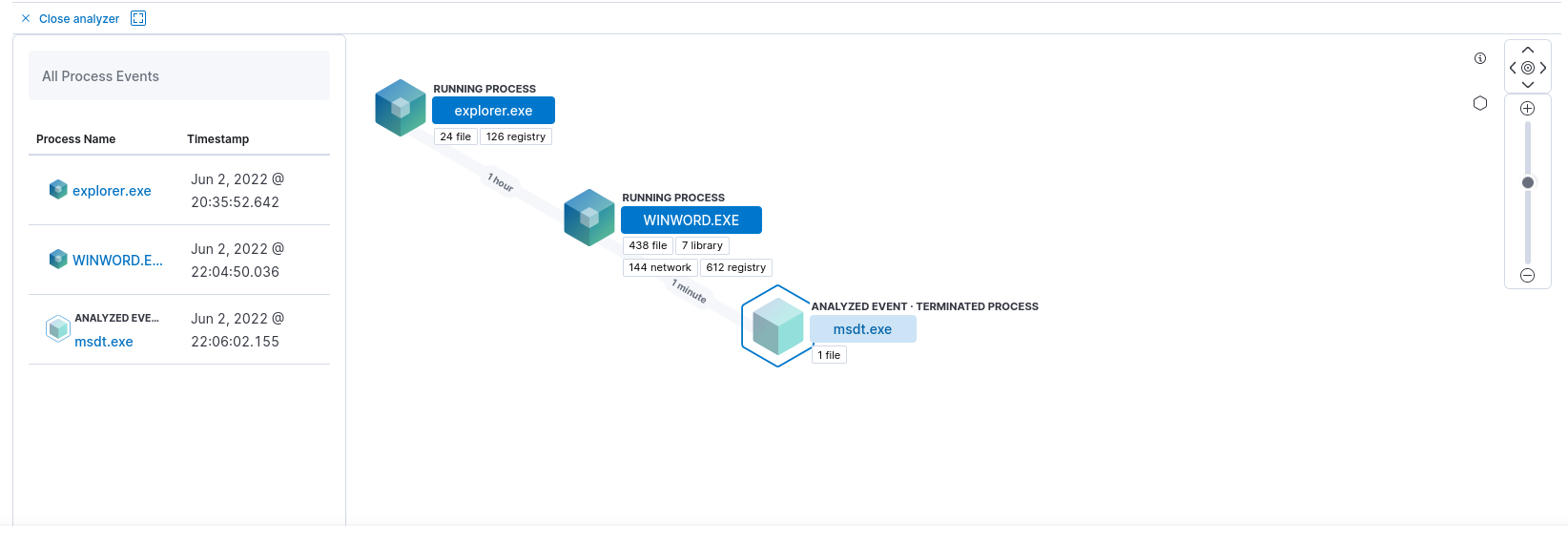
When we investigate the infection more deeply, we find out that the process stems from a suspicious Microsoft office child item. The rule even describes that these child processes are often launched during the exploitation of Office applications or from documents with malicious macros.

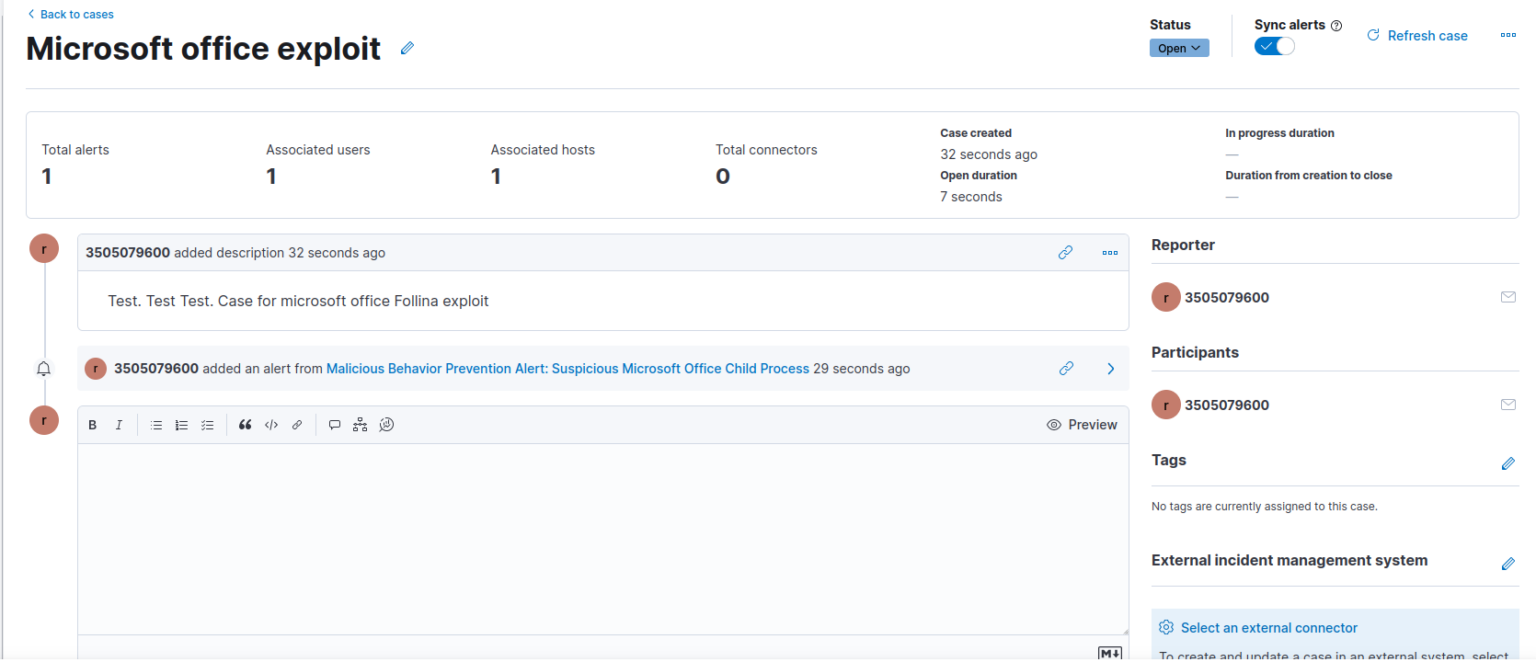
Using this information, we can launch a more thorough investigation with the case function. This makes it possible to work more effectively with a bigger team on incidents, as well as coordinate further investigations accordingly.
CONCLUSION
The test demonstrated how critical 0-day vulnerabilities do not have a fix available by the producer, which leaves many devices vulnerable. Luckily, Elastics endpoint protection not only stopped the process before harm could be done to the system but also carries the capabilities to effectively find the cause of the infection with a very user-friendly environment, making it easy to understand the process behind the infection.
Be warned that the Follina Exploit has already been used in the wild by TA413 CN APT, a Chinese hacker group that used URLs to deliver ZIP archives containing infected Word Documents. Other Hacker groups such as Fancy Bear have also used this exploit already.
ELK FACTORY
Elk Factory is an Elite Elastic Partner for the Benelux. If you have any concerns or questions regarding your cybersecurity setup. Do not hesitate to contact us.
SUBSIDIES BY THE FLEMISH GOVERNEMENT
Small to medium-sized enterprises in the Flemish region receive subsidies of up to 45% to deploy or expand their cybersecurity setup. For more information please read our blog (NL) regarding KMO subsidies or simply reach out to us.

