
RANSOMWARE: PREVENTING WANNACRY ATTACKS WITH ELASTIC
In this blog post, we will explore how Elastic Security handles a WannaCry ransomware attack on a host.
RANSOMWARE
Ransomware is a popular form of malware used by cybercriminals to encrypt and render computers unusable, denying users access to their files and systems. The criminals then demand ransom to return the computers. An example of this is the WannaCry attack that occurred in 2017, which affected hundreds of thousands of computers worldwide and caused millions of euros in damage to businesses.
ELASTIC SECURITY
Elastic Security is a major player in the cybersecurity industry. It allows you to protect, investigate, and respond to complex threats by unifying the capabilities of SIEM, endpoint security, and cloud security.
SIMULATION
SCENARIO
As an employee, you receive a phishing email stating that you need to download a new antivirus from your company. Once you click on the link, a WannaCry virus is downloaded onto your computer.
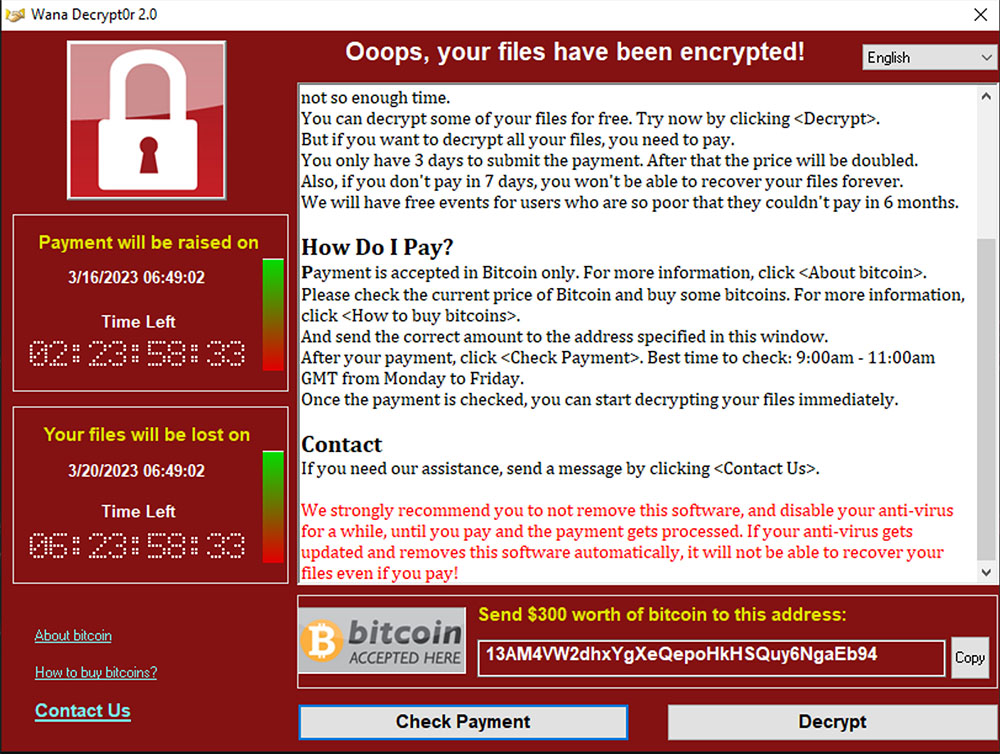
SETTING UP THE EXPERIMENT
To simulate this attack, we need 2 virtual machines: 1 for the attacker (Kali) and 1 for the victim (Windows). First, we start by downloading a WannaCry ransomware sample from The Zoo (a GitHub repository with live malware samples) on the attacker’s device.
ATTACKER KALI
Start by downloading the ransomware sample, which can be found on TheZoo GitHub repository. For this experiment, we will use WannaCry.
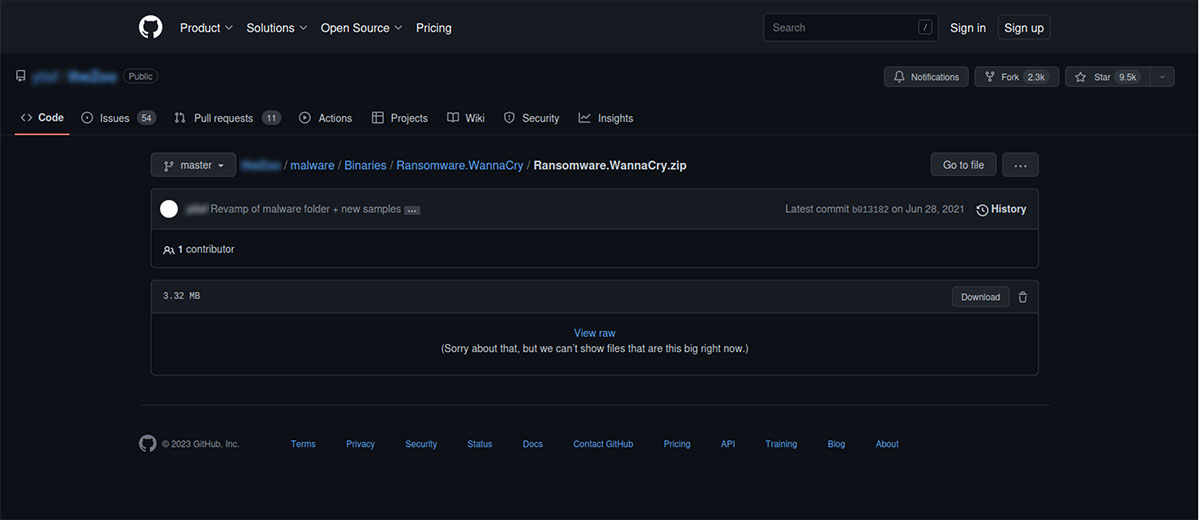
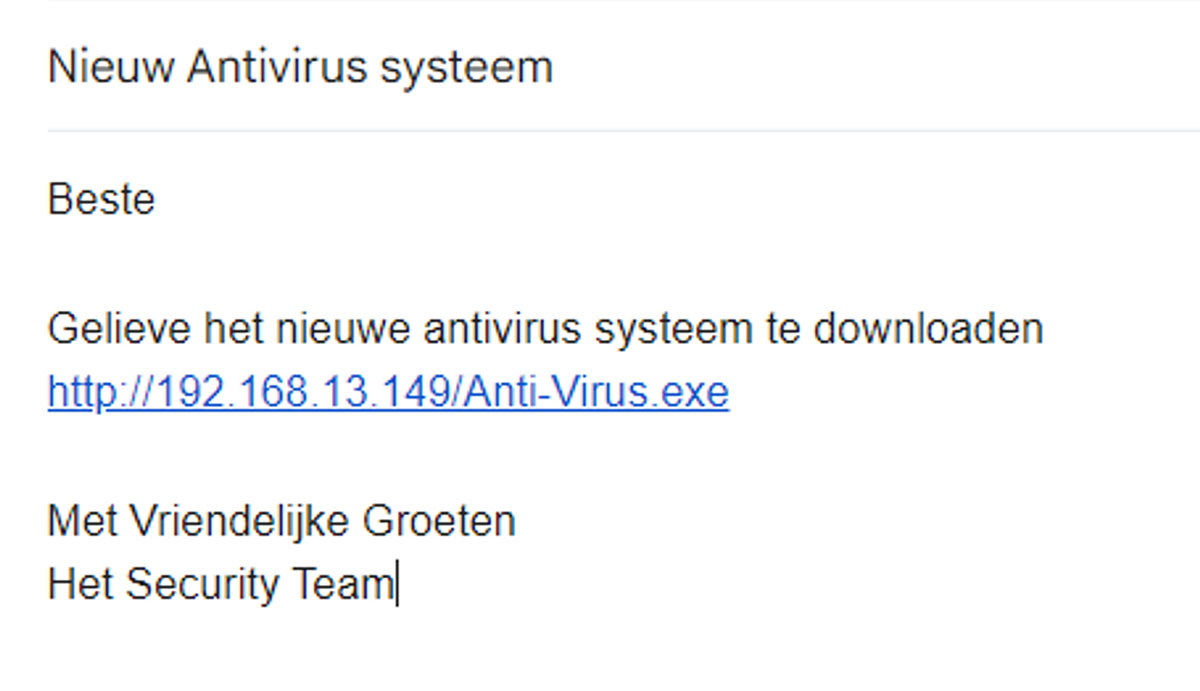
Once the zip is downloaded, extract the sample using the password infected. Rename the file to Anti-Virus.exe. We can then move it to an Apache web server to deliver it to the victim.
To move it, use this command:
mv Anti-Virus.exe /var/www/html
Start the Apache webserver:
service apache2 start
Once the webserver is started, you can download the sample from:
http://192.168.**.***/Anti-Virus.exe
This is the link that would be in the phishing email. Send yourself an email to your own email address so that it can be opened on the victim’s VM.
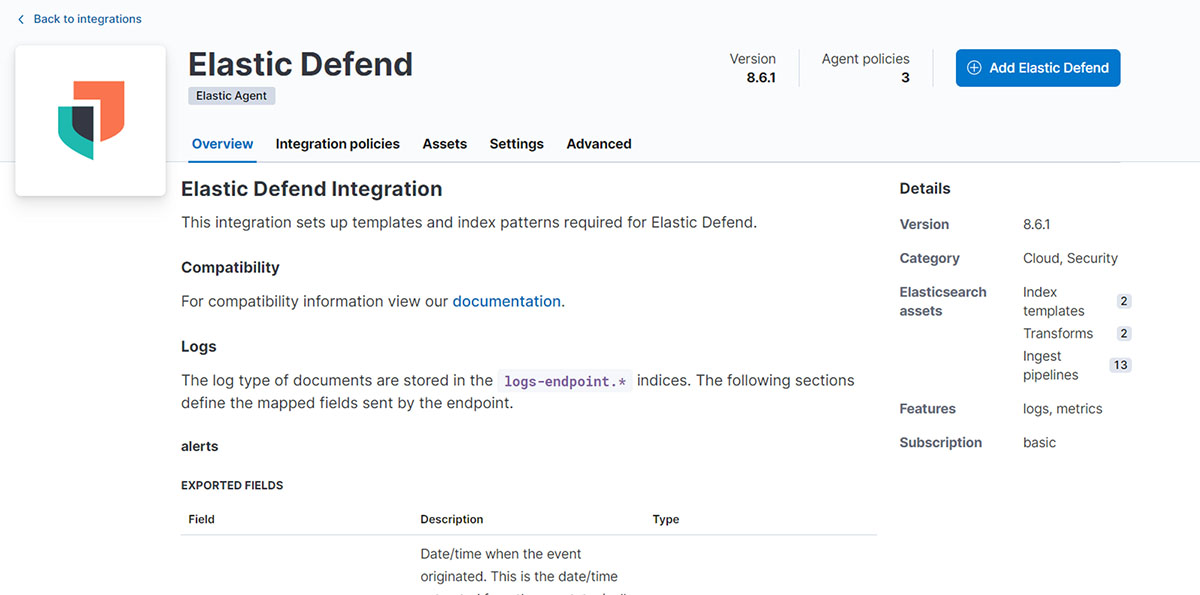
ELASTIC DEFENSE
Ensure that the host being tested has Elastic Defend integration. This will provide the necessary protection, and no specific rules need to be enabled.
VICTIM WINDOWS
To make sure we were testing Elastic Defend, we have disabled Windows Defender. Then, we opened the link in the email that downloads the virus. Elastic Defend immediately removes the file, and the downloads folder is empty. So, there is no chance to execute it.
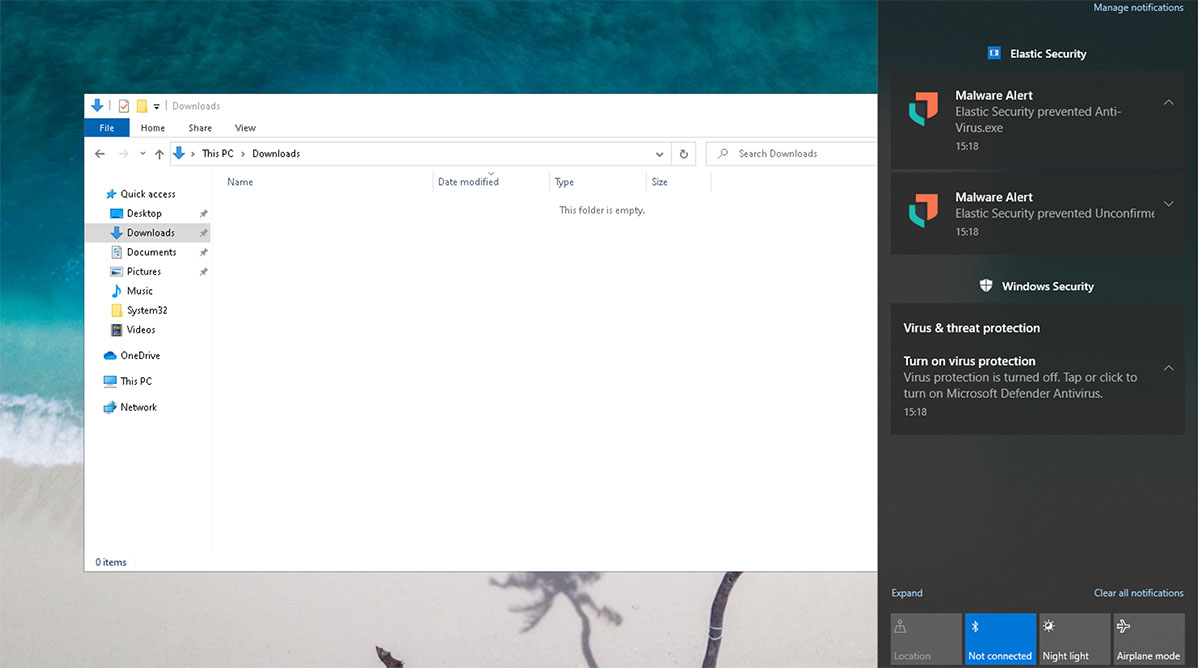
ELASTIC DEFEND RESPONSE
In Elastic Defend, there are 2 alerts indicating that malware has been prevented: 1 for the download and 1 for the Anti-Virus.exe file. From here, you can also create a timeline and case of the alerts to further analyze them. For example, you can see which processes are involved in the malware.
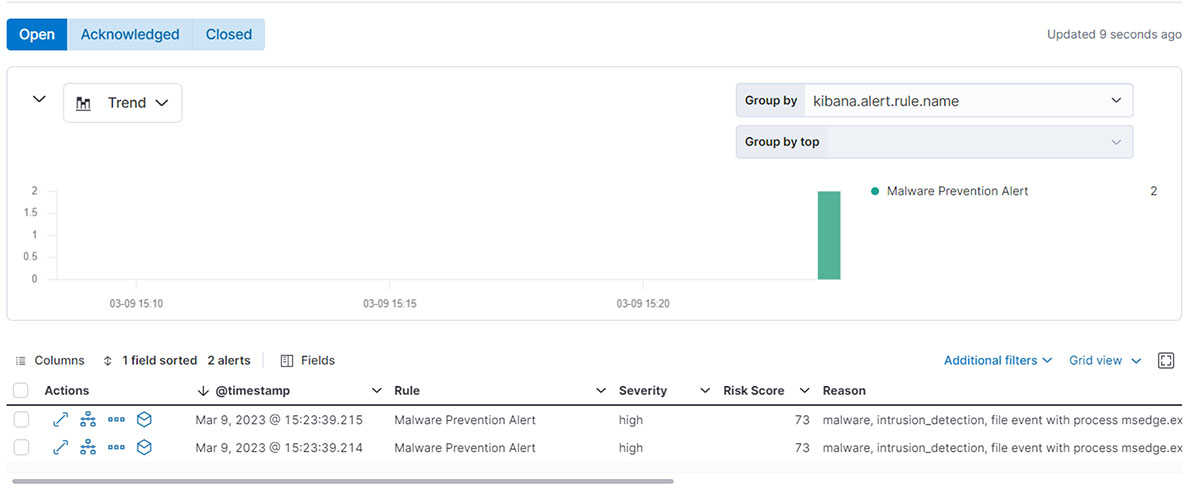
CONCLUSION
Ransomware attacks are a real threat to businesses and governments. Therefore, it is essential to remain protected. In this blog post, we demonstrated how Elastic Security can help prevent ransomware attacks.
It is important to note that in addition to Endpoint Security, Elastic also provides full-fledged SIEM and Cloud Security within the same platform to achieve “XDR” (eXtended Detection & Response). Additionally, Elastic provides a powerful Observability solution within the same platform.
This makes Elastic the best choice to achieve different use cases with the same technology in a highly efficient manner.

